You put on your black hoodie, install Kali Linux, change your Facebook cover photo to edgiest pic related to hacking that you can find and boom! hacker mode. Hell yes, you’re ready to become the next Elliot Alderson and hack the FBI with your 1337 command line tools, that router in your neighbour’s living room that you always wanted access to, and …. let’s just take it back a couple of steps, shall we?
Cybersecurity isn’t like it is shown in the average Hollywood show or movie. It is an art, it consists of many smaller forms of art. I’ll talk about a few of them today.
If we strip everything down, cybersecurity is basically “protecting computer systems from theft or damage”. Sounds simple enough right?
Maybe. But, the field of cybersecurity is huge and there are a lot of branches coming out of it. And while learning about cybersecurity and its fields can make you the hacker you always wanted to be, you’re probably gonna find it easier (and definitely less/not illegal) to practice hacking ethically through bug bounty programs and research. More on that later.
Let’s take a look at a few of the fields you can start studying today, sorted from easiest to hardest, in my opinion. That does not imply that reverse engineering is hard, it is just not as easy for the average beginner. You still have to give it a try before you judge anyway.
Keep in mind that this guide is by no means the “perfect roadmap coming from an expert”. I am just a security enthusiast who happens to have a blog.
So please, check it out and also check out what other security enthusiasts are saying and then try and decide what works best for you.
Web Security
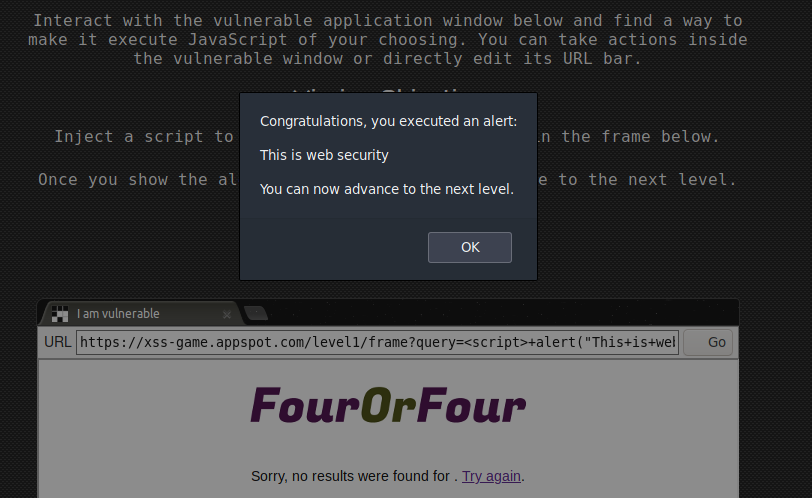
The art of exploiting web applications, websites, servers, and the vulnerabilities related to them.
Web security is a great place to start if you want to get straight into bug bounty programs.
Bug bounty programs on sites like HackerOne, are programs where companies ask you to test their programs, mobile apps, websites, web app, etc.. and submit any security flaws that you find. You get a reward for every bug you find and report successfully.
A Small Example
A website has an issue with filtering input, and you can give it certain input to gain access to private information or the database.
Check out these 2 videos to get a general idea:
- Running an SQL Injection Attack – Computerphile
- Cracking Websites with Cross Site Scripting – Computerphile
Resources
- Courses:
- Web Application Penetration Testing Course Instructed by Ebrahim Hegazy
- Hacker 101
- Cybrary
- Paid courses like SANS SEC401.
- Books:
- Mastering Modern Web Penetration Testing by Prakhar Prasad
- The Tangled Web: A Guide to Securing Modern Web Applications by Michal Zalewski
- Web Hacking 101 by Peter Yaworski
- The Web Application Hacker’s Handbook by Dafydd Stuttard
- Interesting stuff:
Thanks to Aly Anwar and Amr Fathi for recommending most of these resources.
Digital Forensics
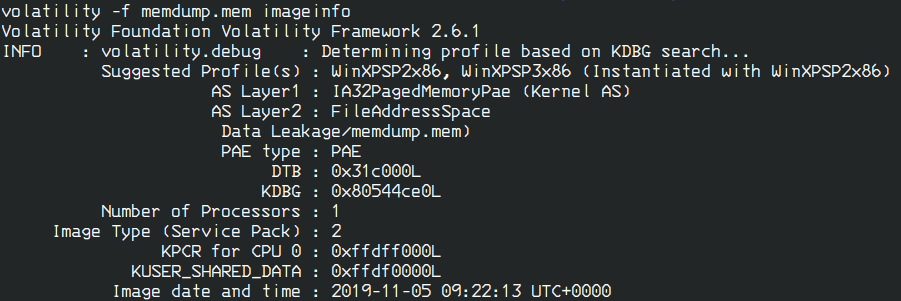
The art of analysing the footprints and the evidence. The art of backtracking.
This branch of cybersecurity focuses on the analysis of traces and captured files such as captured network traffic, recovered hard drive images, memory dumps, etc..
It is basically tracing back the steps that caused the attack, crash, exploit, etc…
Analysis is usually done through tools that help you examine the evidence(files) you have at hand so that you can get to the tiniest of details.
It’s also worth noting that there is a branch of digital forensics called steganography, which is the art of hiding messages in other messages. Such as hiding text in an image or a file in a video.
A Small Example
A server was running and then crashed because of a malware. You can then analyse the memory dump that was produced at the time of the crash to trace back what caused this to happen.
Check out these 2 videos to get a general idea:
- Digital Forensic Memory Analysis – Volatility
- Secrets Hidden in Images (Steganography) – Computerphile
Check this write-up for a good example too:
Resources
- Courses:
- 13Cubed Youtube Channel
- Cyber Triage/Autopsy DFIR Training
- A few forensics courses on OpenSecurityTraining.info
- Paid courses like SANS 500, 508, 518, 526, and the list goes on.
- Misc:
Thanks to 0x01G33k for telling me about some of these resources.
Reverse Engineering
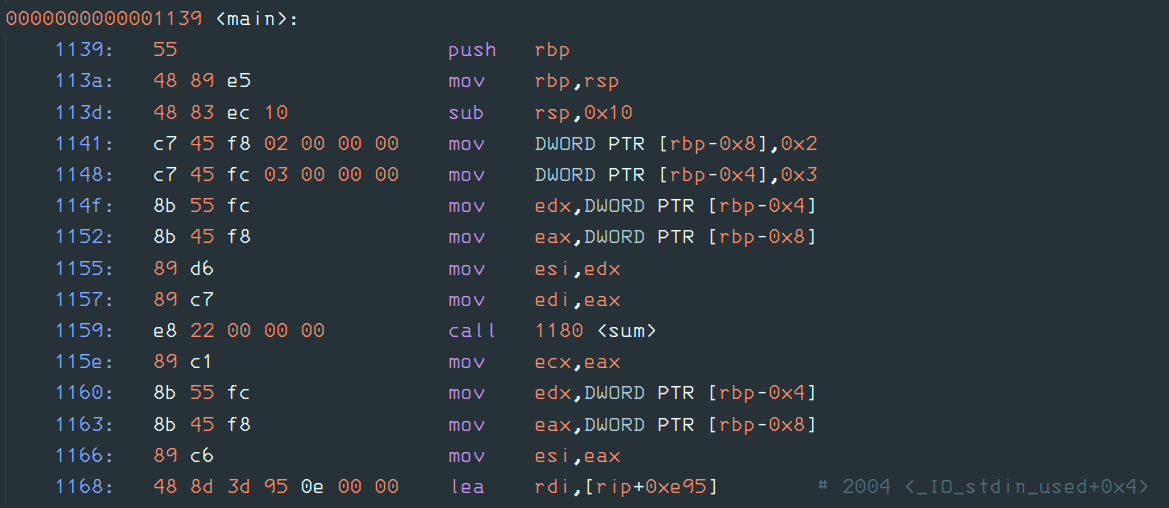
The art of analysing and exploiting binaries.
This branch of cybersecurity focuses on the analysis of binary files. Including malware, of course.
Analysis of binaries is usually done using disassemblers or decompilers which assist in reading the binary file in assembly language (or even high level code in some cases).
A Small Example
A malware hits a company’s server. To clean up, you have to know what the malware did exactly and try to: A, disable it, and B, fix the damage done completely.
Check out these 3 videos to get a general idea:
- MMORPG Bot Reverse Engineering and Tracking - LiveOverFlow
- Introduction to Reverse Engineering | Ollydbg Tutorial - The PC Security Channel
- Buffer Overflow Attack – Computerphile
Resources
- Courses:
- OpenSecurityTraining.info (Literally one of the best)
- Start with Intro to x86 and then check out the maps on the site to continue in one of the reverse engineering paths.
- Ranjeet Mewada’s Youtube Channel
- Malware Unicorn
- Reversing Hero
- beginners.re
- OpenSecurityTraining.info (Literally one of the best)
- Reading Material:
Of course, that’s not all.
There are many many more fields, to name a few:
- Cryptography
- Network Security
- Binary Exploitation
- Cloud Security
- Blockchain Security
- and much much more.
Now What?
Well, now that you know a little bit about 3 of the major cybersecurity fields, you can start practicing on CTF platforms. Here are a few sites:
There’s also this list that has many many more: fareedfauzi.github.io/ctfonline
You can start with PicoCTF as it is the easiest and learn as you go as the challenges are really beginner friendly at first and then gradually get harder.
Once you find yourself liking a certain type of challenges, you can start studying it more in depth and solving CTFs of that type on other sites as well.
All you’ll need is your mind and a search engine.
You can also check out Wargames at OverTheWire. I recommend that you start with Bandit.
Other Relevant Resources
- CTFs
- Linux Resources
- Youtube Channels
- SECRET HACKER FORUM
- An Overview of Cryptography – Gary C. Kessler
I hope that this guide was enough to get you sort of started with cybersecurity.
You may feel lost at first and that is completely normal as it is a huge field.
I’ve updated this guide a lot since it was first written. So, please, if you have any recommendations for study material, by all means tweet them at me, or email/dm them to me and I’ll add them to this guide or any future upcoming articles if the material doesn’t fit here.
Share this guide with your friends if you found it useful. As always, thanks for reading!
